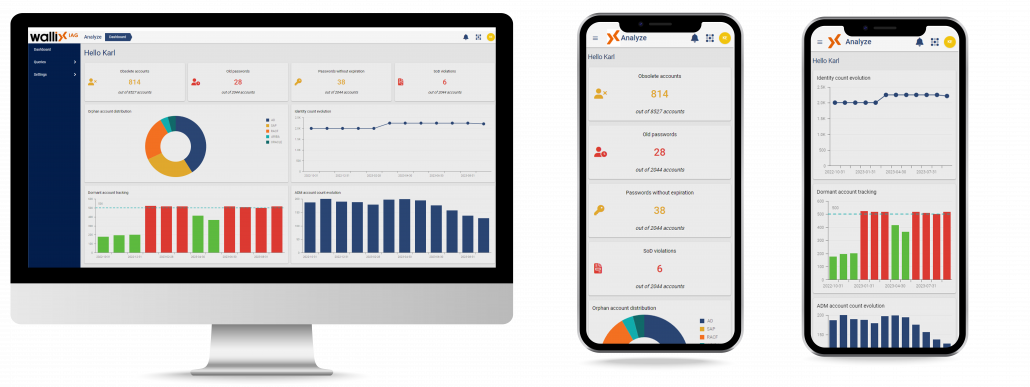
WALLIX IAG
Seamlessly provides a comprehensive mapping of identities to their respective permissions. Whether you’re overseeing access certification campaigns or tracking staff changes, our solution acts as a control tower for all your business applications.